A major trend in application deployment over the past few years has been the use of containers.
Containers allow users to build and promote an application and its dependencies as a unit, and unlike traditional virtualization (VMs), they do not need a hypervisor. This is because containers virtualize application processes instead of hardware. As an example, we can easily deploy multiple applications on a single host, spinning up and shutting down individual containers as needed. This provides benefits such as portability and efficiency and eliminates the need to manage guest operating systems on VMs.
Adoption of container technology has increased significantly over the past few years. Many enterprises are using or planning to use container engine technology. Docker is the leading choice for a container engine.
But as with all popular solutions, Docker containers have become a prime target for cybercriminals. In the past two years, several security issues have been exposed allowing cryptojackers to exploit Docker containers by backdooring and installing reverse shells and cryptocurrency miners. Malicious Docker container images have been uploaded to the Docker Hub (Docker’s official repository). If these containers are downloaded and used, they, in effect, turn an application into a piece of malware. According to Kromtech, 17 malicious Docker images have been found on Docker Hub.
Enterprises should be making an effort to ensure that their products are secure. This is a very broad requirement with a lot of pieces. We can now add another piece to this effort, ensuring the security of Docker containers that are used. Here are two initial tips to start with.
Host OS and Kernel security
Containers share the host operating system kernel, so security starts with the host. If the host is compromised, all processes can be vulnerable, and this, of course, includes the isolated container environment. It is extremely important to keep the host operating system properly patched and updated and make sure to apply all security configuration to keep it safe. A good attention to virtualization libraries such as `libcontainer`, `libvirt`, and LXC should be given as the container engine relies on it.
Image Authenticity
The Docker image is the base of a running container. There are several Docker images on Docker Hub that provide a base OS as well as drop-in solutions we might be tempted to use along with our application. We need to know and/or check the authenticity of those images before pulling them and using them.
The Docker Hub provides three useful filters:
- Docker Certified: Docker Certified images are built with best practices, tested and validated against the Docker Enterprise Edition platform and APIs, pass security requirements, and are collaboratively supported.
- Verified Publisher: High-quality Docker content from verified publishers. These products are published and maintained directly by a commercial entity.
- Official Images: Docker Official Images are a curated set of Docker open source and “drop-in” solution repositories.
Here is a screenshot from Docker Hub:
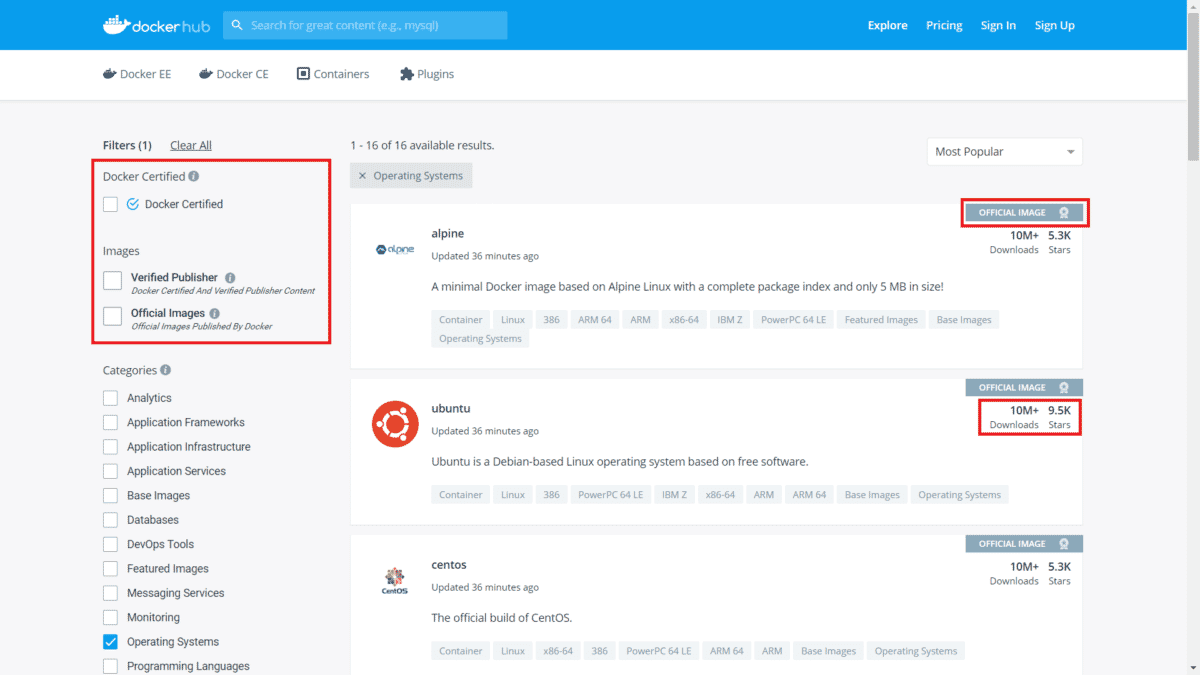
If the image you need does not meet one of the filters above, check the number of downloads and stars. In addition, it is important to read the documentation provided by the author as well as the Dockerfile and its declared commands looking for suspicious instructions.
Also, the ‘docker search’ command can also be used to search for images without accessing the Docker Hub Web UI. e.g., docker search redis –filter “is-official=true”
At IP Infusion, we strongly advise and guide our customers to follow the best security practices while implementing container solutions in their products. In the final part of the “How Secure are Your Docker Containers?” we present more advanced tips to make sure you can follow the best practices to secure your containers.

