Network communications and automotive transportation often share terminology. A term used frequently in both is ‘bridges’. With road traffic, bridges are structures that allow traffic to move from one area to another. For example, in eastern Canada, the Confederation Bridge allows traffic to flow from Prince Edward Island to New Brunswick (and the rest of the Canadian mainland).
In networking, the device used to connect multiple networks together at layer 2 (L2) is called a bridge. Layer 2 refers to the data link layer of the OSI model, where data is encoded into units (frames), checked, and transmitted. The bridge has interfaces to several LAN segments which it connects (or bridges) together. Ethernet bridges have been around since the mid-1980s. Operation of a bridge was first standardized in IEEE Std 802.1D in 1990. Since 2000 (roughly) most bridges have been based on IEEE Std 802.1Q, which introduced support for virtual LANs (VLANs) through a method of tagging frames with additional information.
Often the term “switch” is used instead of “bridge”. In reality, an Ethernet Bridge and an Ethernet Switch are the same thing (the only term used in the standards is “bridge”), but “switch” came into vogue to describe a bridge with more than two ports. But the term “switch” is frequently used for technology that is not bridging (e.g., an MPLS switch) so “bridge” is still the preferred term.
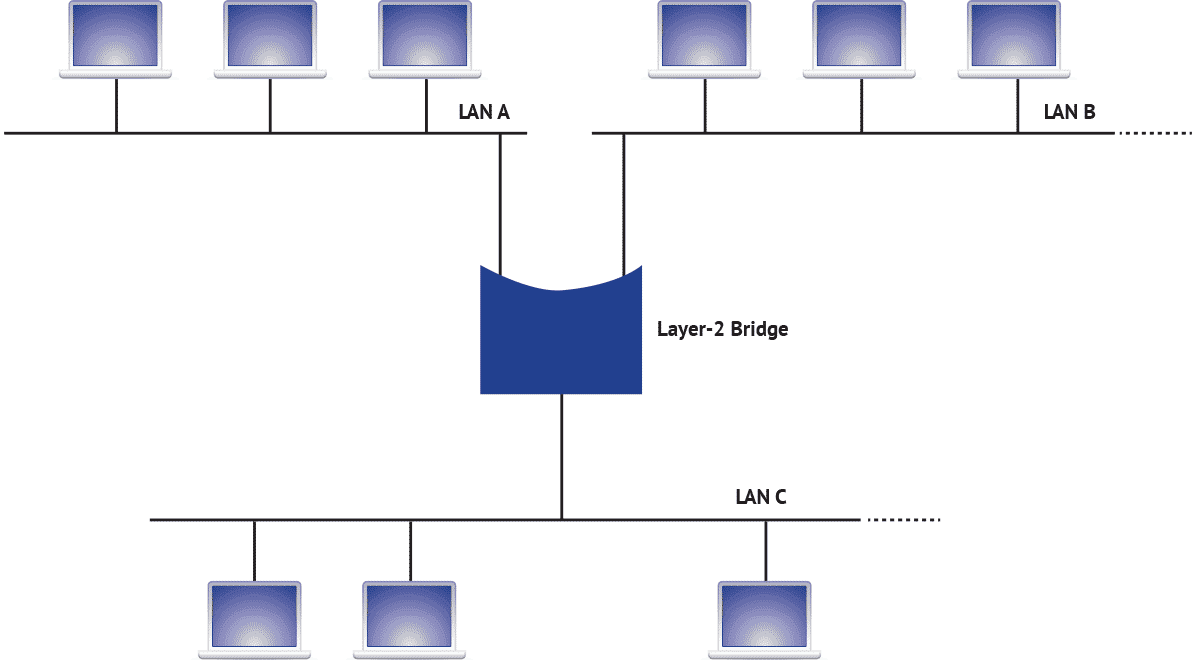
A bridge operates by examining each frame and referring to the media access control address (MAC address) values included within the frame to specify the source and destination.
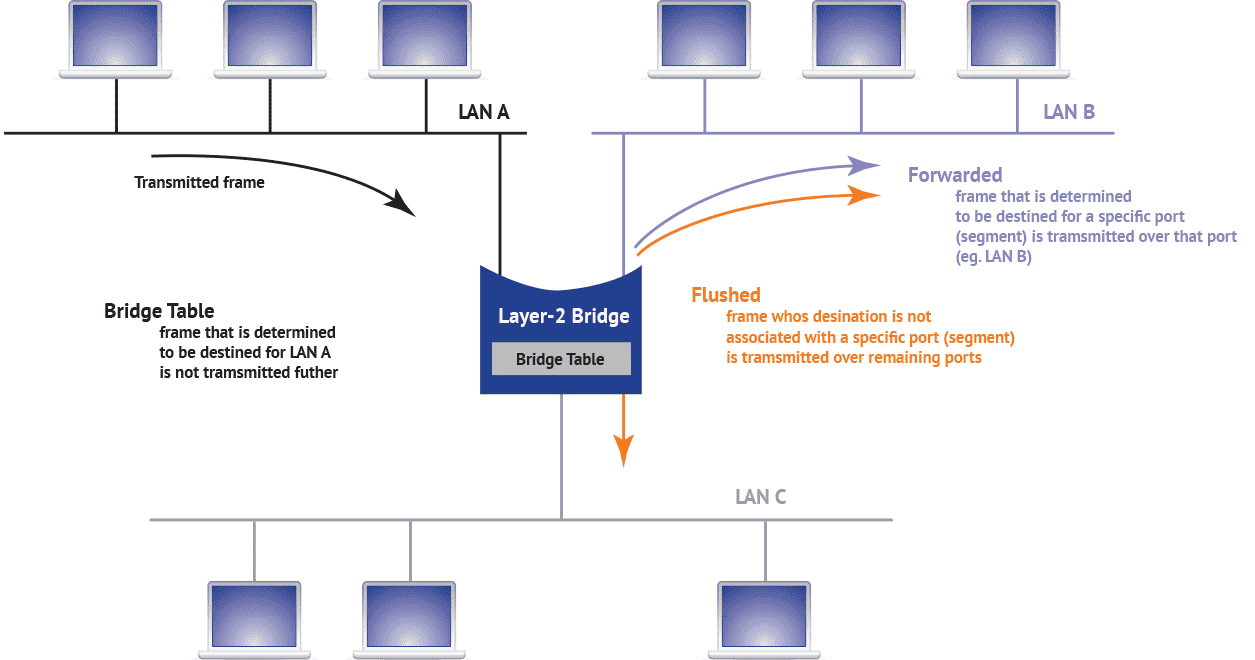
The bridge extracts the source address of each frame received on its interfaces (ports) and store the address in a bridging table along with the port it was received on. This is called “learning” because the bridge learns where each MAC address is located relative to itself (i.e., which port can be used to reach the MAC address). MAC addresses that have no activity for a configurable amount of time (default is 5 minutes) are removed from the table.
When a frame is received by the bridge, the bridging table is used to decide how the frame will be handled. If the frame is not destined for the bridge itself, it will be filtered, forwarded, or flooded. If the destination address is found on the same port as the frame is being received it is filtered and is not processed any further. If the destination is found in the table and it is not on the same port, it is forwarded on through the port that is associated with it. If the destination address is not found in the table, it is flooded–transmitted on all the ports, except for the one where it was received. Frames destined to broadcast and multicast addresses are also flooded. There is potential for forwarding loops to be created depending upon how bridges are implemented. To prevent this situation, additional protocols, such as Spanning Tree Protocol, have been developed to detect loops and break them by disabling some bridge ports.
On Linux systems, the primary functionality of a layer-2 bridge can be observed using a software bridge implemented at the kernel layer using the bridge module. The brctl command can be used to create bridges, add interfaces, remove interfaces, and to view the bridging table.
Layer 2 bridging is fundamental to network communications. Bridging creates the ability to extend Local Area Network functionality and connectivity across a much broader area than the LANs themselves can span and are much easier to configure than routers (layer 3 connectivity). Bridging has some scaling limitations but using bridging to build extended LANs and then connecting these extended LANs together with routers (connectivity at layer 3) allows the creation of large, complex network implementations that meet today’s requirements.
Bridging is a function that spans a wide variety of network technology. In virtualization, we can combine switch functionality with other network functions and create complex dynamic configurations. With the advancements in Passive Optical Network (PON) technology, bridging protocols are linking devices at higher speeds, and with increasing capacity. Northforge has the expertise and experience with these concepts and technologies that can be leveraged to create powerful solutions.
Our domain knowledge extends these basic concepts of bridging into areas of virtual LANs and tagging, layer two supporting protocols (such as STP – Spanning Tree Protocol) and beyond. Using industry leading devices and APIs from Broadcom, Northforge delivers custom solutions that can optimize switch hardware platforms, providing switching solutions with hundreds of terabits of bandwidth.

